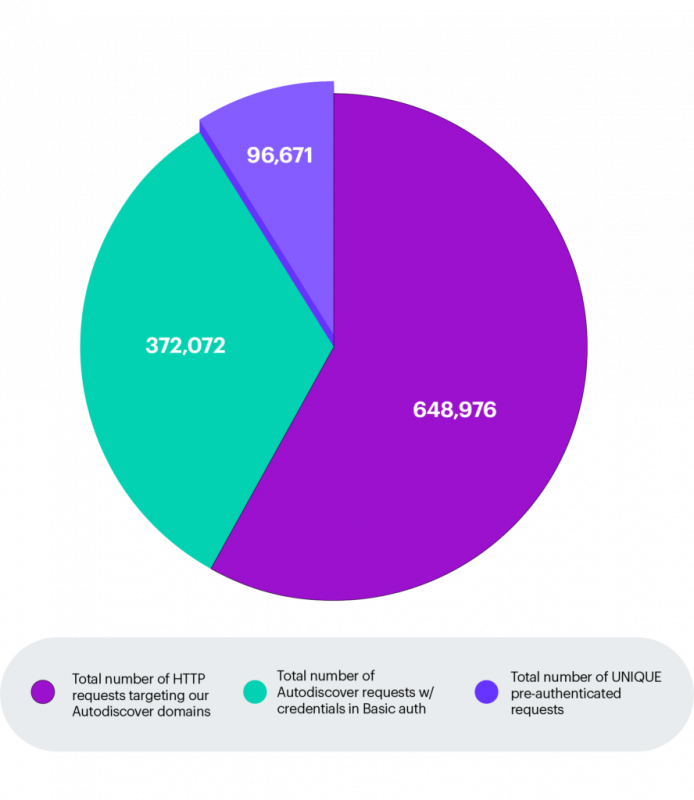
Recently a “design flaw” in the Microsoft Exchange’s Autodiscover protocol was discovered by researchers that allowed access to 372,072 Windows domain credentials and 96,671 unique sets of credentials from applications such as Microsoft Outlook and third-party email clients. According to Amit Serper , the person who discovered the flaw, the source of the leak is comprised of two issues; the design of the Autodiscover protocol, more specifically the “back-off” algorithm, and the poor implementation of the protocol in some applications.
This severe security issue allows an attacker that is able to sniff the network or control specific domains to capture domain credentials in plain text (HTTP basic authentication). In addition, when attackers have the ability to conduct large-scale DNS poisoning attacks, they could collect valid domain credentials on a large scale compromising the security of many businesses.
The AutoDiscover service constructs a list of endpoints using the provided domain name where the autodiscover.xml file is typically found. When configuring a new e-mail account in your e-mail client application, the e-mail client tries to build the URL using the domain name in the following format:
- https://autodiscover.domain.com/autodiscover/autodiscover.xml
- http://autodiscover.domain.com/autodiscover/autodiscover.xml
- https://domain.com/autodiscover/autodiscover.xml
- http://domain.com/autodiscover/autodiscover.xml
When none of these endpoints are responding the “back-off” procedure is started which is where the design flaw lies. When all endpoints fail the next attempt to retrieve the autodiscover.xml will be pointed at the following URL:
http://Autodiscover.com/Autodiscover/Autodiscover.xml
This means that whoever controls the autodiscover.com domain is able to receive all requests that fail to reach the original domains. The researchers have purchased several TLD variants on Autodiscover (such as Autodiscover.fr and Autodiscover.com.co) and assigned these to a web server where a significant number of requests to Autodiscover endpoints came in with a populated Authorization header. The requests originated from various verticals ranging from investment banks to power plants and manufacturing companies.
To mitigate this security issue organizations can establish their own Autodiscover domains and block all other autodiscover.TLD domains at the firewall or in the local DNS. The security issue is also caused by poor implementation of the AutoDiscover protocol in e-mail clients. Software vendors can prevent the issue by not letting the application fail into the “back-off” procedure where the autodiscover.TLD domains are constructed. Moreover, system administrators should disable support for basic authentication when deploying Microsoft Exchange servers. This prevents clear-text credentials being send over the network which can be easy to intercept.
Conclusion
It is important to understand that credentials to login to an Exchange based e-mail box are often domain credentials. The impact of leaking domain credentials on such a large scale is enormous if you realize that they can be used to compromise e-mail accounts (especially when 2FA is not configured). The consequences can be disastrous for the targeted company as a compromised business e-mail accounts can be used to access sensitive data in the mailbox, reset passwords and even perform social engineering and ransomware attacks that could lead to significant financial losses. Leaked domain credentials can also be used to gain an initial foothold on the network through internet exposed services such as SSL VPN, Remote Desktop Gateways (Yes, internet facing RDP gateways still happen!) and possibly even through an unpatched Exchange server.
More detailed information from the researchers who discovered the flaw in the Microsoft Exchange AutoDiscover service is available here:
https://www.guardicore.com/labs/autodiscovering-the-great-leak/
https://docs.microsoft.com/en-us/exchange/client-developer/exchange-web-services/autodiscover-for-exchange
Penetration Testing Microsoft Exchange
Are you interested in learning more about Microsoft Exchange Penetration Testing? Check back the Hacking Tutorials website again soon as we’re working on an Exchange Penetration testing tutorial series.
Hacking Courses on Udemy
Bug Bounty – An Advanced Guide to Finding Good Bugs
Real World Bug Bounty Techniques

Website Hacking / Penetration Testing & Bug Bounty Hunting
Become a bug bounty hunter! Hack websites & web applications like black hat hackers and secure them like experts.

















