In this tutorial we will be installing OpenVAS on Kali linux. OpenVAS is an advanced open source vulnerability scanner and manager and can save you a lot of time when performing a vulnerability analysis and assessment. Using an automated up-to-date vulnerability scanner in penetration test often helps you to find vulnerabilities which can be easily overlooked during a manual assessment. The OpenVAS scanner uses more than 47.000 Network Vulnerability Tests (NVTs) as of June 2016.
In this tutorial we will be installing OpenVAS on the Virtual Kali Linux machine we’ve installed in an earlier tutorial. If you haven’t installed Kali Linux yet we recommend you to do that first. The OpenVAS installation process is rather straight forward but might need some explanation along the way. After the installation process is finished we will be scanning the Metasploitable 2 vulnerable machine we’ve installed earlier in the Metasploitable 2 installation tutorial for known vulnerabilities.
OpenVAS installation
Let’s start with installing OpenVAS and run the following commands in a terminal session to download and install OpenVAS:
apt-get install openvas
openvas-setup

The last commands is setting up OpenVAS and is synchronizing the NVT feed with the NVT collection on your machine. Depending on your connection speed this might take a while to finish.
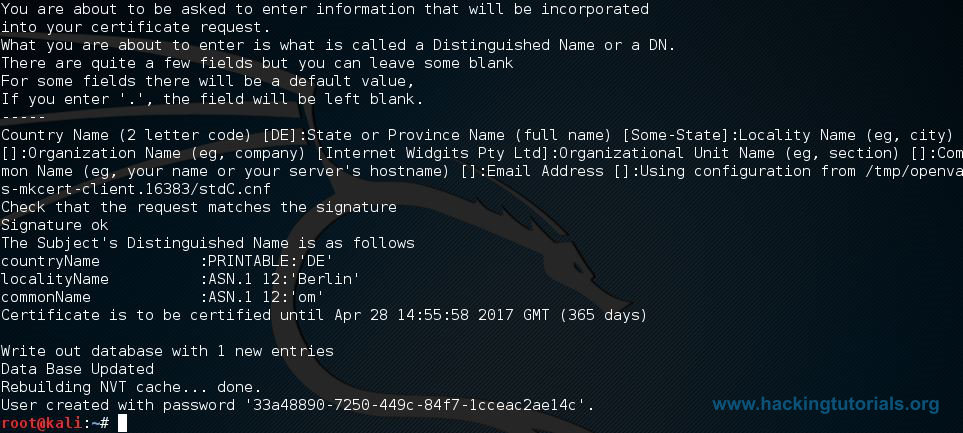
When the installation process is finished you will be presented a long password on the last line of the console. This password is used to login to the OpenVAS web interface so you need to save it somewhere and change it after the first login.
When the OpenVAS setup process is finished the OpenVAS manager, scanner and services are listening on port 9390, 9391, 9392 and on port 80. You can use the following netstat command to check if these services are listening:
netstat –antp
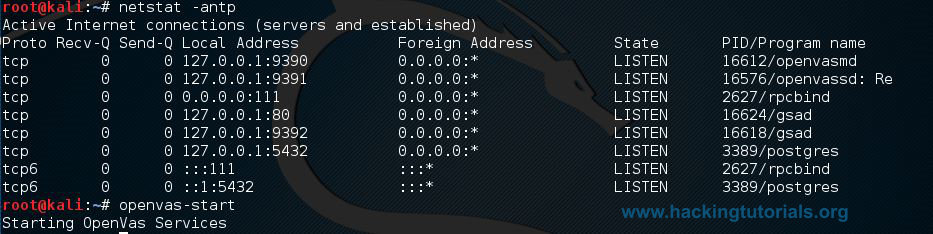
Netstat –antp command Explained
-a all
-n show ip instead of host names
-t show only tcp connections
-p show process id/name
Running OpenVAS
If the OpenVAS services are not running than use the following command to start these services:
openvas-start
Than connect to the web interface using a browser and point it to:
https://127.0.0.1:9392
Accept the self-signed SSL certificate and sign in with user ‘admin’ and the password generated during the setup process. The web interface after logging in should look like this:
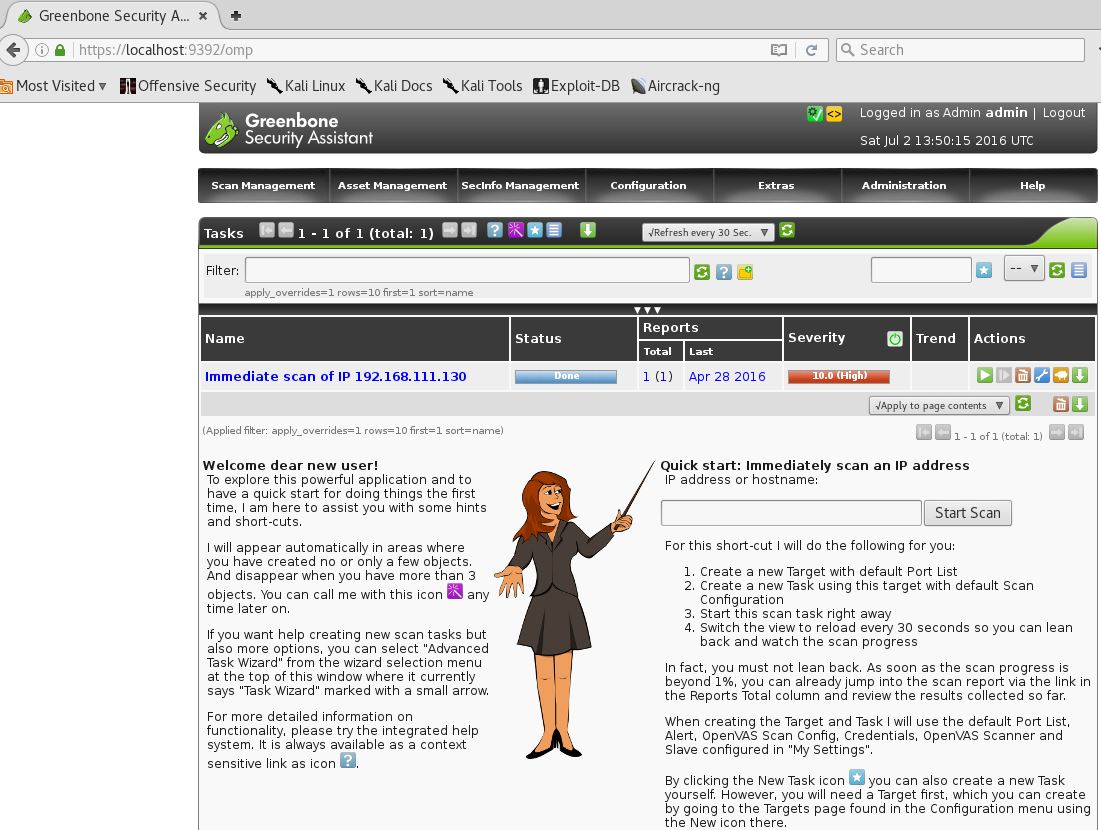
Scanning Metasploitable 2 with OpenVAS
Starting a scan with OpenVAS is very easy and straightforward. Just enter the target’s hostname or IP address in the quick start field and press the ‘Start Scan’ button. Make sure you only scan targets with OpenVAS you physically own or have (written) permission to scan. OpenVAS vulnerability scanner will generate a lot of network traffic which may lead to crashes or DOS.
When the scan is finished click to the reports page under the Scan Management menu and have a look at an overview of the scan results:
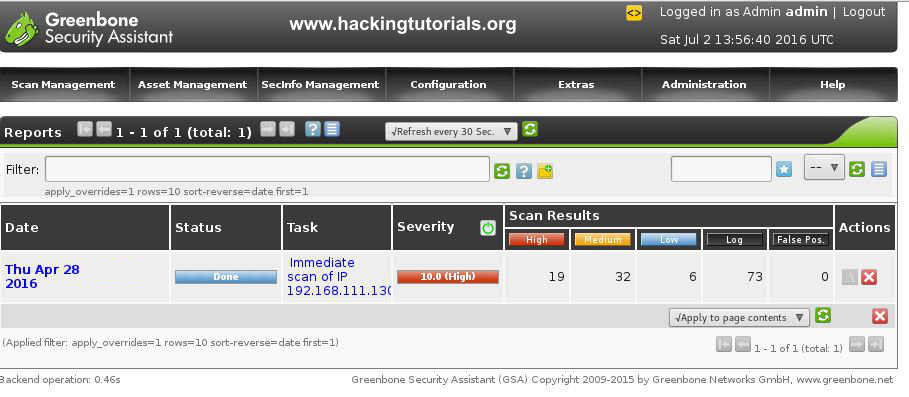
As you can see the Metasploitable 2 vulnerable machine contains 19 high, 32 medium and 6 low rated severity vulnerabilities. When you click on a report you can see a more detailed overview of the found vulnerabilities. The list of known vulnerabilities is ordered on severity:
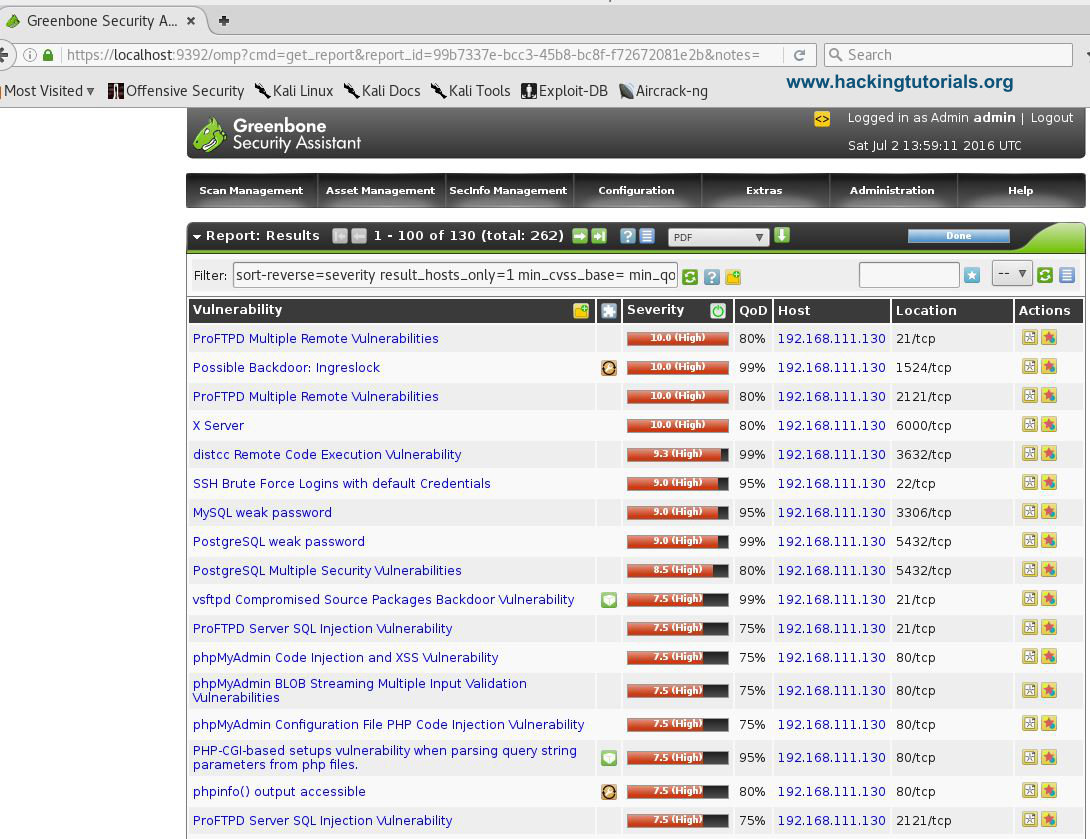
OpenVas offers a lot more functionality, including the vulnerability database from the feed categorized in CVE’s, NVT’s and CPE’s. The SecInfo Management tool also offers a nice dashboard showing some high level statistics on vulnerabilities:
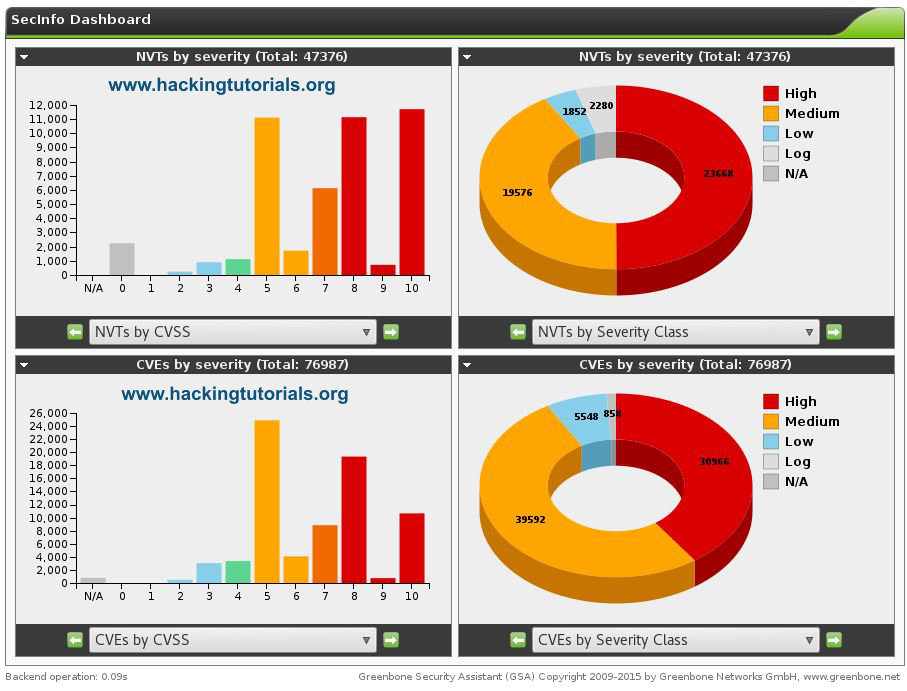
With the vulnerability dashboard we will conclude this tutorial. We recommend you to get familiar with OpenVAS, the reports and the vulnerability database by running more scans and compare the results with other vulnerability scanner. Hopefully this tutorial has proven useful to you and will get you started in automated vulnerability scanner. Happy Scanning!


















