Clipboard Hijacking: What it is, How to do it and how to prevent it.

At the core of the internet browsing experience is the clipboard functionality.
However, this integral component of the browsing experience is not without its vulnerabilities, and clipboard hijacking is a growing concern in the online world.
In this article, we will explore what clipboard hijacking is, how it can be done, and how to protect yourself from it.
What is Clipboard Hijacking?
Clipboard hijacking is the process of intercepting and modifying data that is copied to the clipboard, without the user’s knowledge or consent.
It is a type of cyberattack that targets the clipboard of a device, and it can be used to steal sensitive information such as passwords, credit card details, and other personal information.
We regularly copy and paste stuff. Sometimes, the copied characters contain important information such as bank numbers or crypto wallet addresses. Attackers can replace the copied address with an address under their control. Hence you might accidentally transfer money to an attacker instead of your original target.
I suspect that malware is using the clipboard all the time to steal credentials, but I haven’t found many reputable sources for specific cases:
- 2020: An iOS update revealed, that several apps were reading the clipboard without their user’s knowledge (source)
- 2019: Fake MetaMask App That Hijacks Ethereum dApps was in the Android Play Store (source)
- 2019: The archive server of the PaleMoon browser was hijacked using ClipBanker (source)
Clipboard Hijacking requires malware to be executed on the victim’s machine. It only works on end users’ machines as servers typically don’t have anything in the clipboard.
One common example of clipboard hijacking is when you copy a Bitcoin address from a website to transfer funds. The malware can intercept the address you have copied and replace it with the attacker’s own Bitcoin address. When you paste the address into your Bitcoin wallet, you are unknowingly transferring funds to the attacker instead of the intended recipient.
Reading the clipboard can be done in any language. For example, with JavaScript:
<!DOCTYPE html>
<html>
<body>
<button onclick="readClipboard()">Read Clipboard</button>
Clipboard:
<p id="output"></p>
<script>
function readClipboard() {
navigator.clipboard.readText()
.then(text => {
document.getElementById("output").innerHTML = text;
})
.catch(err => {
console.error('Failed to read clipboard: ', err);
});
}
</script>
</body>
</html>
However, the browser only allows it if the user gives consent. For every single time:
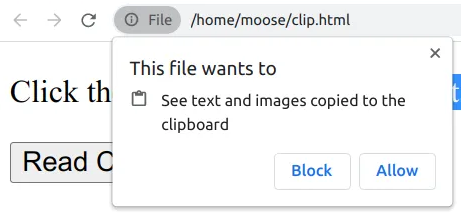
However, browser extensions are a different story.
You can also read the clipboard with Python or any other programming language. There the users are not protected by the operating system. Once the software is installed, it can access the clipboard:
import pyperclip
pyperclip.paste()
Malicious software can be downloaded onto a victim’s computer and can then monitor the clipboard for sensitive information, such as passwords or credit card numbers. Once the malware detects this information, it can send it back to the attacker.
Besides stealing clipboard contents, they can also be manipulated. For example, if the malware detects a bank account number or a crypto wallet address in the clipboard, it could change the contents to the attacker’s address. It can look like this:
import time
import pyperclip
while True:
content = pyperclip.paste()
if content.startswith("0x"):
# Detected a wallet address
attackers_address = "mgk4owiQ4M8WFZBB4KsWUBcZ7m3E4ix4Gy"
pyperclip.copy(attackers_address)
time.sleep(1)
How to Protect Yourself from Clipboard Hijacking?
There are several steps you can take to protect your clipboard from hijacking. Follow these 4 steps to keep your clipboard safe:
Step 1: Keep Your Operating System and Applications Up-to-Date
he first and most important step you can take to protect your clipboard is to keep your operating system up-to-date. Clipboard hijackers often take advantage of vulnerabilities in outdated operating systems to gain access to your clipboard data. Therefore, it’s essential to update your operating system and all the software you use regularly. This will help patch any known vulnerabilities and keep your system secure.
Step 2: Use Antivirus and Anti-Malware Software
Using antivirus software is also crucial in protecting your clipboard. Antivirus software can detect and remove malware that may attempt to hijack your clipboard. Ensure that you use reputable antivirus software and update it regularly to ensure that it can detect the latest malware threats.
Step 3: Be Careful What You Copy and Paste
As we’ve already established, clipboard hijackers can access any data that you copy to your clipboard. Therefore, you should be cautious about what you copy and paste. Avoid copying sensitive data such as passwords, credit card numbers, or other personal information. Instead, consider typing the information manually or using a password manager to protect your sensitive data.
Step 4: Use a Clipboard Manager
A clipboard manager is software that saves all the data you copy to your clipboard. It allows you to access your clipboard history and reuse previously copied data. Using a clipboard manager can help protect your clipboard because it prevents clipboard hijackers from accessing your sensitive data. When you use a clipboard manager, your sensitive data will remain encrypted, and you can delete any sensitive data from your clipboard history.
Conclusion
In conclusion, clipboard hijacking is a serious security concern that can result in the loss of sensitive personal information. By understanding how it works and taking the necessary precautions, you can protect yourself from falling victim to this type of cyberattack. Make sure to keep your browser up to date, avoid untrusted sources, and be vigilant when using the clipboard. By taking these steps, you can help ensure your online safety and security.


















1 Comment